-
The WalletConnect app hack on Google Play masqueraded as a legit wallet—accumulating over 10,000 downloads and siphoning $70K from 150 users.
-
Hackers used fake reviews, rebranding, and deep-link phishing to drain high-value tokens first, highlighting critical flaws in current app vetting.
-
Users and platforms must embrace robust security practices—careful app vetting, transaction monitoring, and AI-powered scam detection—to safeguard crypto assets.
The unmasking of the WalletConnect app hack has sent ripples throughout the entire ecosystem.
According to Check Point Research, the hackers launched crypto wallet scams on Google Play for over five months without alarming any security checks.
This feat underscores the rising threats surrounding digital assets, with the franchise becoming more mainstream as governments push for adoption.
WalletConnect is a stark reminder that Web3 wallet security is vital as decentralized finance begins to dominate the finance sector.
These latest incidents question how to unmask wallet drainer scams infiltrating trusted platforms and how best to improve upon standard crypto wallet security tips.
WalletConnect App Hack Exposes Critical Web3 Wallet Security Flaws on Google Play
According to the findings, the WalletConnect app hack leveraged several key factors, such as changing its name from Mestox Calculator to leveraging fake reviews and eventually branding to impersonate WalletConnect.
This led to many unannounced users directly downloading the phishing application, garnering over 10,000 downloads.
Eventually, the exploit was launched targeting WalletConnect, a dependent protocol for connecting crypto wallets with decentralized programs.
The Web3 wallet security breach employed faux options and steady branding that enabled it to rank within Google, including victims into thinking they had the genuine article.
The concept of crypto wallet scams on Google Play was a small topic until the WalletConnect app hack reminded us that hackers are also adapting to the change.
How the WalletConnect App Hack Unfolded
However, the crypto hack continues masquerading as a functioning application to deepen its grip on the user’s account. The crypto wallet drainer diverts users to a malicious website, luring unexpected victims.
Upon masquerading as the legitimate application, the wallet drainer diverted users to a malicious site while they connected to the legitimate wallets. Their perpetrators employed state-of-the-art hacking techniques like clever contracts and deep links.
CHECK OUT: From Cold War Bunker to Luxury Stay: Solana Doomsday NFT’s Bold Plan.
These lecherous tactics maximized income by first prioritizing higher-price tokens for withdrawal, prioritizing those with greater returns earlier than targeting smaller belongings.
Unfortunately, from a financial perspective, the Google Crypto Scam has caused the organization about $ 70,000 stolen from 150 compromised crypto wallets.
The crypto bull run, which introduced millions to the crypto space, has provided the perfect opportunity for hackers.
Implications for Users and Industry
While Google Play enforces permissions reviews and malware scans, the evolving sophistication of wallet drainers suggests convectional checks just won’t cut it.
As technology continues advancing at breakneck speed, so too do the tactics employed by cybercriminals seeking easy targets among everyday consumers and seasoned investors alike.
Learning how to protect crypto assets from malware apps is not necessary, given the current rage of the ongoing bull run.
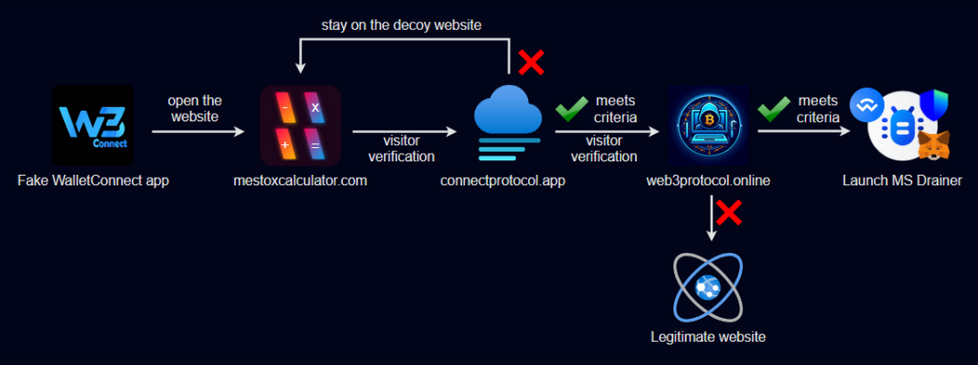
A diagram of how the fake WalletConnect app worked to drain certain user funds. [Photo: Check Point Research]
Web3 Wallet Security has improved, but user accountability has grown even more crucial.
The WalletConnect app hack is among many reminders that Web 3 and crypto still have some ways before becoming mainstream.
How to Unmask Wallet Drainer Scam Tactics
To safeguard against crypto wallet scams on Google Play and other platforms, users should employ several security measures:
1. Be Wary When Downloading Apps
Always be aware of what kind of applications you intend to use. Crypto trading has become a steady income source for many individuals but also serves as a pool of resources for hackers.
2. Monitor Wallet Activity Regularly
Users should robotically monitor crypto transactions to perceive any unanticipated pastime that might indicate hacks. Early detection can drastically mitigate ability losses.
3. Stricter App Store Verification
Google Play and comparable systems must quickly decorate their verification procedures to hit upon fraudulent apps earlier than they attain customers. Incorporating AI-powered detection techniques or undertaking thorough guide opinions mainly centred on financial packages.
4. Promote User Education
Initiatives designed to teach users about Web3 wallet security risks can arm them with the necessary knowledge to understand scams and implement protective measures.
The Web3 industry is an ever-evolving franchise. Today, we have several branches, such as digital assets, NFT, DeFi, and fintech. To better understand these, one must have due diligence to safeguard their wallets within each branch.
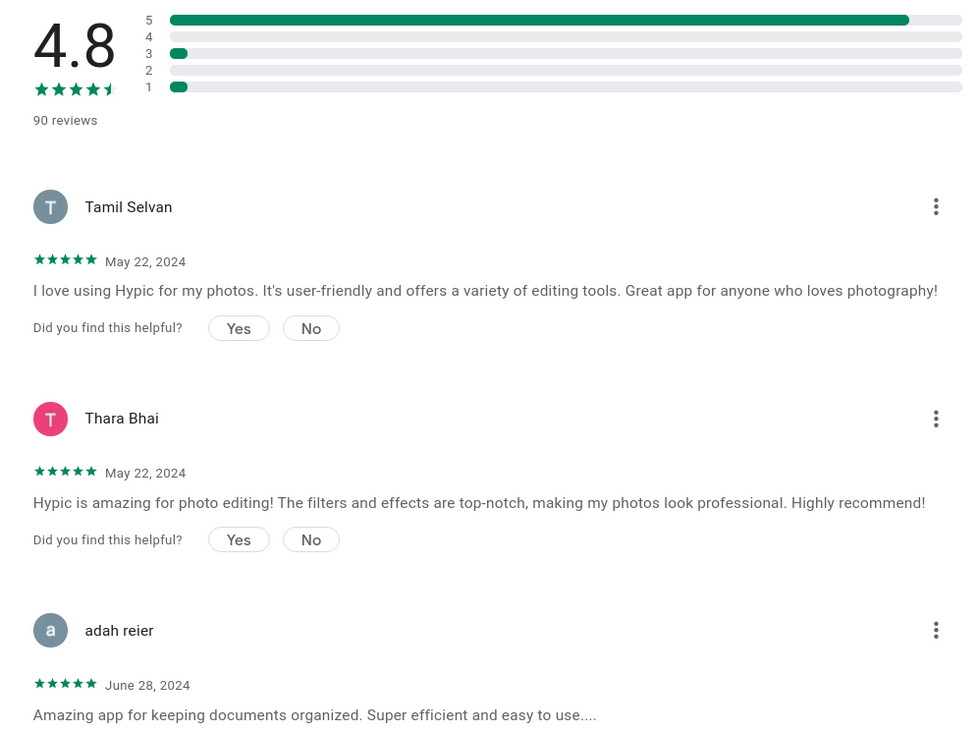
Some of the faked reviews on the spoofed WalletConnect app mentioned features that had nothing to do with crypto. [Photo: Check Point Research]
Securing the Future of Web3
The WalletConnect Scam is a stark reminder that as the crypto bull run continues to make millionaires, the likelihood of crypto wallet security issues increases.
The WalletConnect app hack served as a sobering reminder that the crypto bull run is an opportunity to make millions or lose everything.
The wallet drainer has pocked a hole into blockchain security, questioning whether Web2 applications are ready for the financial revolution digital assets bring.
Thus, consumers, stakeholders, traders, and innovators need to prioritize security to prevent a similar crypto hack from occurring.
Each participant in a surroundings bears the obligation to adopt several crypto wallet security tips to prevent such a scenario from befalling them.
Stay vigilant: learning how to unmask wallet drainer scams and questioning app legitimacy are non-negotiable skills in today’s digital economy. As Check Point’s report proves, complacency is the true enemy.

